IT Service Catalog
Innovative XaaS and IT Management Solutions
What is an IT service catalog?
Service catalog can be of two types.
1. Business service catalog
2. Technical service catalog
Why do you need an IT service catalog?
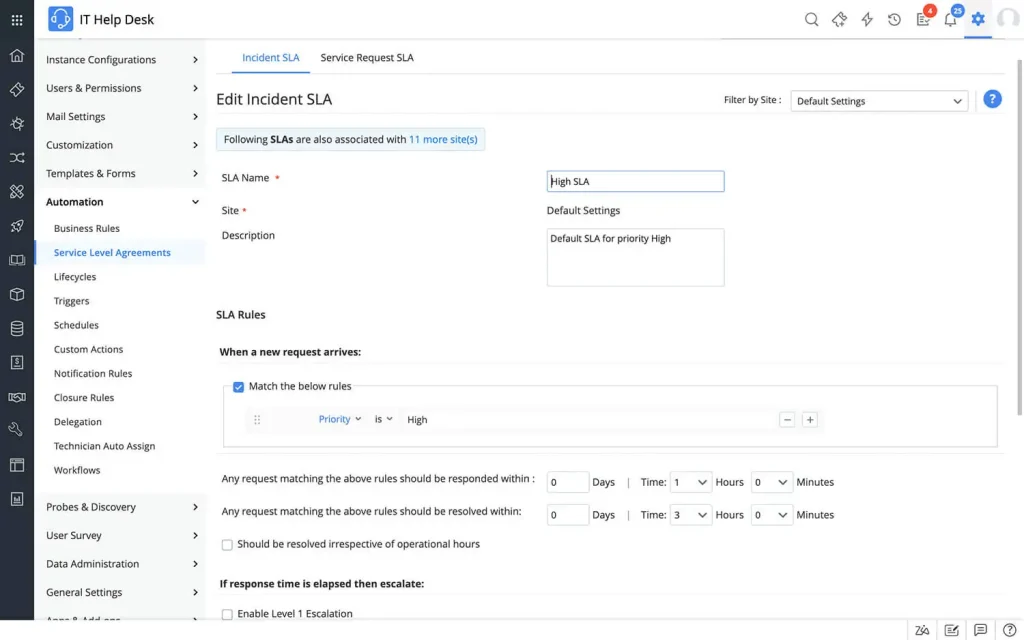
Service catalog best practices in ITSM :

Provide a simple, business-facing description of the service (description)

Identify a service owner (technician, groups)

Service availability (publish to relevant user groups)

Mention service level targets (SLAs)

Define authorization, escalation, and notification policies (Approval details, notification rules)

Specify costs
(additional fields)
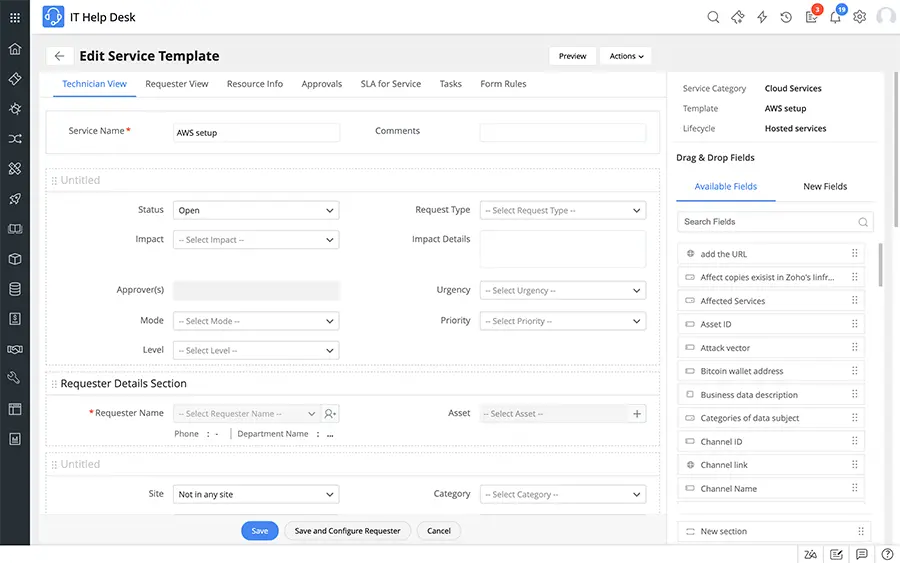
Design and Publish IT Services Quickly
– Associate workflows like SLAs, multistage approvals, and tasks to make work easier for service desk technicians.
– Access a wide range of pre-built service request templates and customize them to your needs with minimal effort.
Drive a Compelling Shopping Experience
– Promote self help and improve operational efficiency.
– Allow users to create and track their service requests on the go.
– Keep end users informed at every step for better visibility and transparency.
– Provide anytime anywhere access to end users by showcasing the service catalog in the self-service portal.
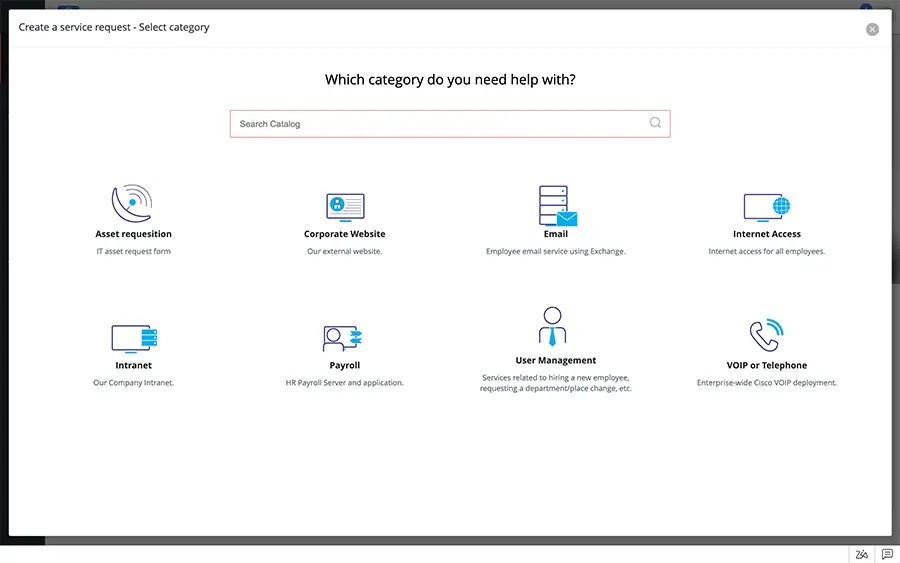
Automate for Efficiency. Optimize IT Service Delivery.
– Promote self help and improve operational efficiency.
– Allow users to create and track their service requests on the go.
– Keep end users informed at every step for better visibility and transparency.
– Provide anytime anywhere access to end users by showcasing the service catalog in the self-service portal.

Innovative XaaS and
IT Management Solutions Architecture
Key Challenges Addressed by
Innovative XaaS and IT Management Solutions:
Rising Cyber
Threats
Protect exposed networks as businesses shift online, eliminating vulnerabilities with proactive threat detection.

Complex Tech Demands
Simplify operations with a unified platform that adapts to new technologies, reducing the burden on IT teams.
Workload Overload
Automate repetitive tasks like log analysis, configuration management, and performance tuning.
Skill Gaps
Leverage expert-driven solutions and a user-friendly portal to bridge talent shortages and standardize operations.
Smart essentials to make your ITSM wholesome
Make service management cross the boundary from IT to other business processes with the ITSM
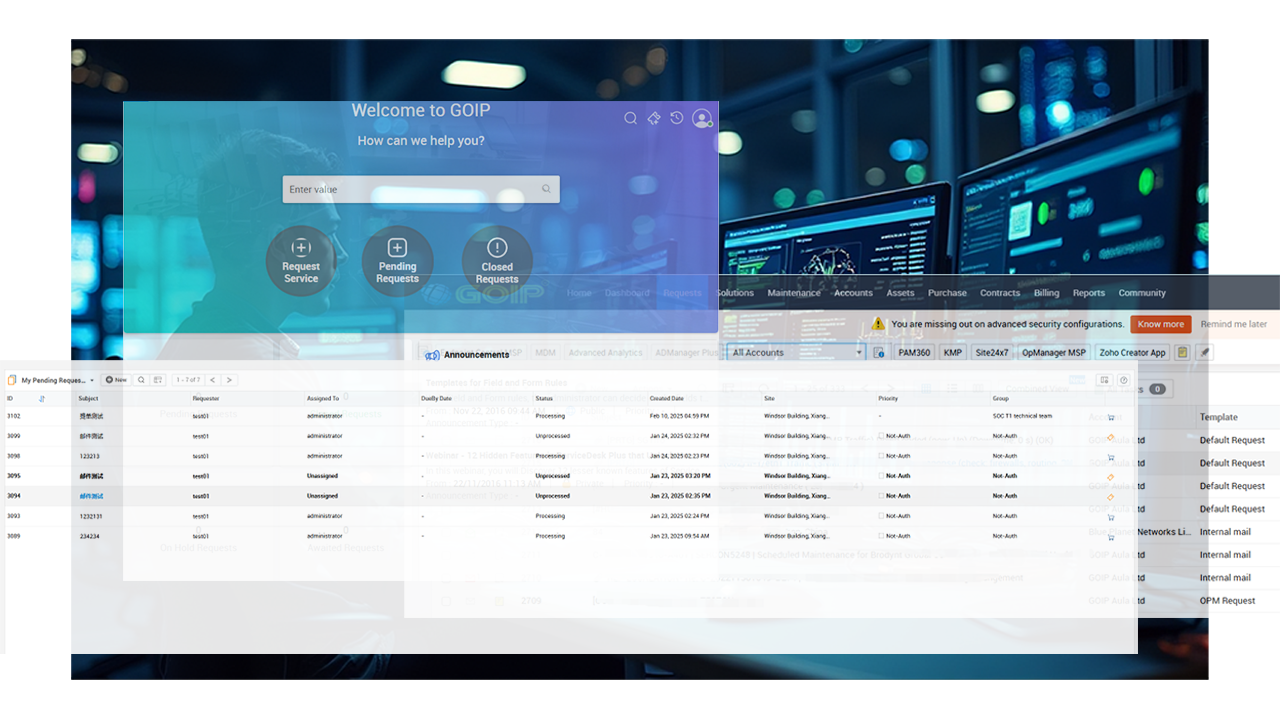
ITSM Platform
Overview:
ITSM is the “heart” of the Innovative XaaS and IT Management Solutions, serving as the core platform for managing customer network issues and incident reporting effectively. It provides a standardized operational method for Innovative XaaS and IT Management Solutions.
Key Features:
24/7 Instant Ticket Creation and Response:
Experience rapid ticket creation and processing that aligns with customer service agreements. Receive updates via email, SMS, and WeChat, while also allowing for web-based ticket tracking and history retrieval.
Network Management System (NMS)
Core Functionality:
The Network Management System is the central feature of the Innovative XaaS and IT Management Solutions, focusing on the operational stability and security monitoring of network devices. With 24/7 monitoring of customer-connected devices, it triggers response rules for instant ticket creation, connecting engineers to resolve issues and inform users.
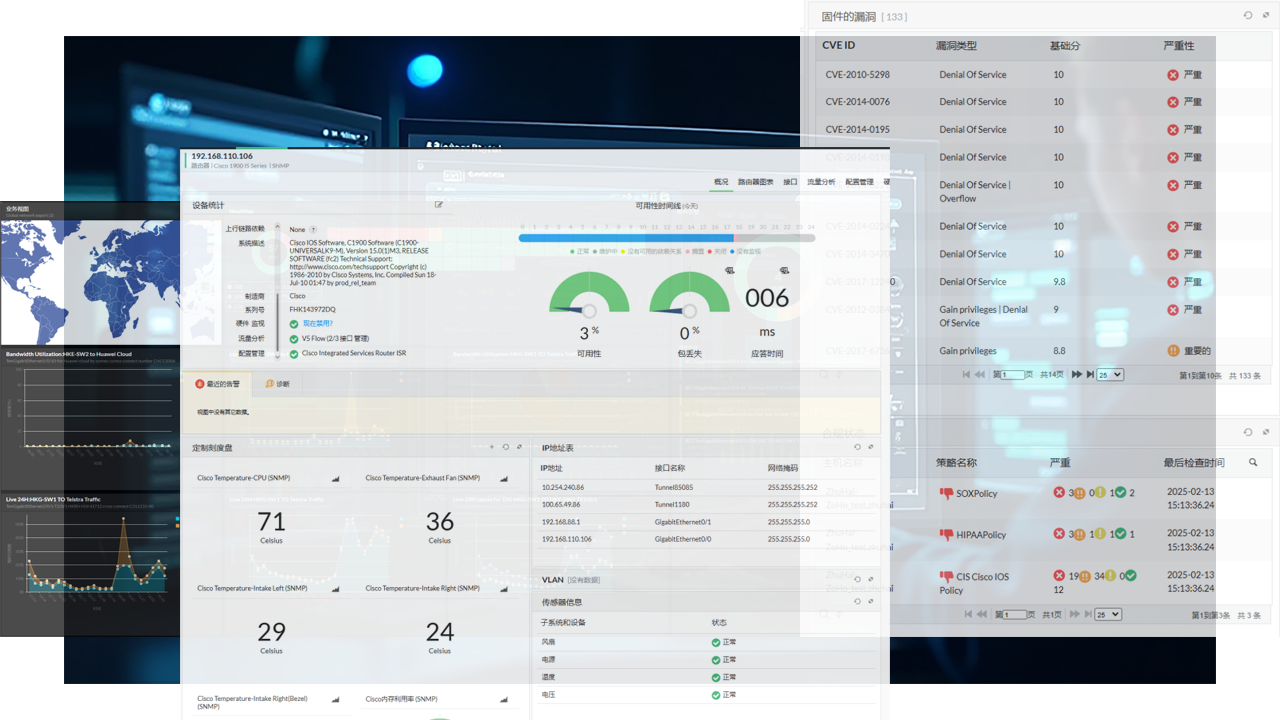
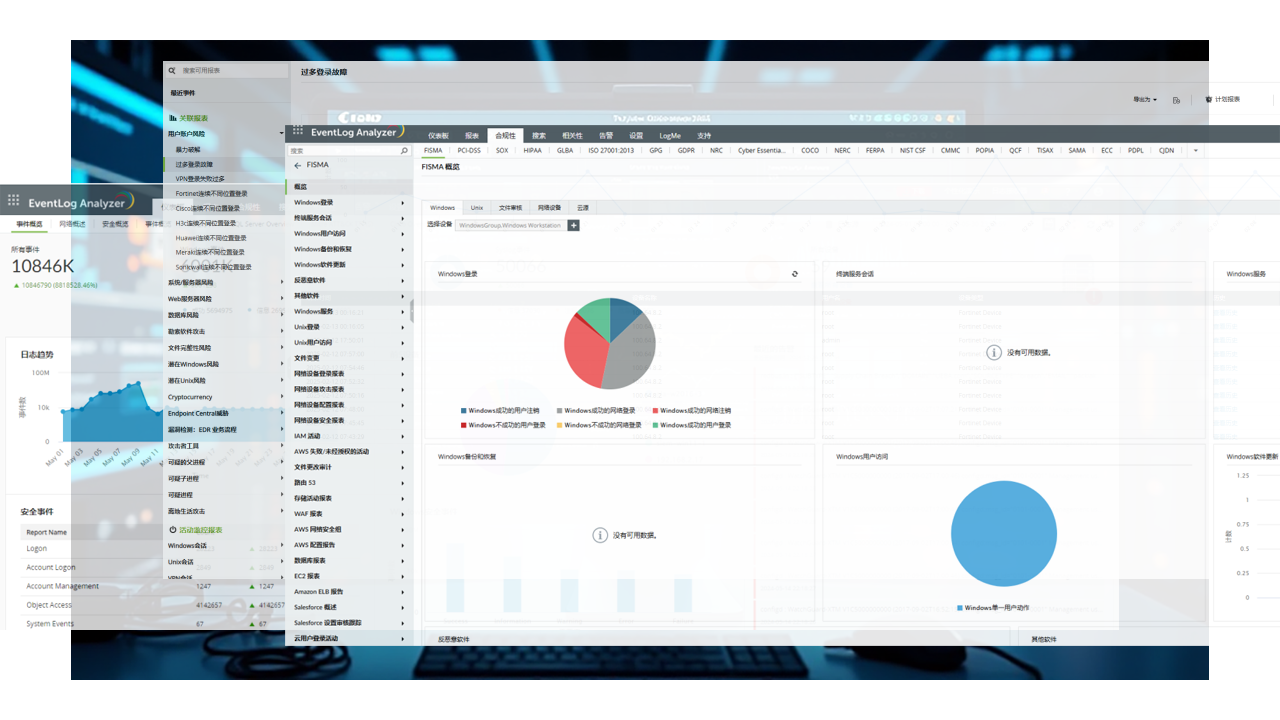
EventLog Analyzer Platform (ELA)
Security Analysis Tool:
EventLog Analyzer Platform is a critical component of the S.NOC solution for network security analysis. It collects logs from servers, network devices, security equipment, and application systems to conduct thorough security assessments.
The platform offers compliance checks for network security and performs standard baseline security evaluations on devices. It integrates with the ITSM system to set response rules for instant ticket creation, facilitating timely issue resolution and user notifications.
Why Choose Innovative XaaS and IT Management Solutions?
Unlocking Your Business Potential
Continuous oversight of devices, traffic, and logs for instant anomaly detection.
Automate workflows, generate real-time reports, and resolve incidents faster.
Track every action with a dedicated dashboard for audits, compliance, and transparency.
Security
Stay ahead of threats with AI-driven analytics and adaptive response protocols.

