Security Information
and Event Management (SIEM)
Accelerate Your Log Analysis Process and Get Ahead of Threats with EventLog Analyzer
What is
Security Information and Event Management (SIEM)?
Imagine a central nervous system for your organization’s security defenses. SIEM combines advanced analytics, automated threat detection, and unified data correlation to monitor your entire IT ecosystem 24/7. This proactive technology collects and analyzes security data across networks, devices, applications, and cloud environments – transforming fragmented clues into actionable intelligence.
SIEM Solutions
Fortifies your business with enterprise-grade SIEM technology. Our platform acts as your always-on security sentinel, leveraging real-time threat detection, automated incident response, and predictive analytics to shield your operations. Focus on growth while we ensure uninterrupted security.
What does
SIEM Do?
– 24/7 Threat Monitoring: Continuous surveillance across all assets and locations.
– Automated Incident Response: Instant threat neutralization powered by AI-driven workflows.
– Proactive Vulnerability Management: Identifies risks before exploitation through behavioral analytics.
– Unified Compliance Reporting: Simplifies audits with centralized logs and real-time dashboards.
SIEM provides an intelligent security shield – enabling faster responses, reduced risk, and strategic peace of mind.
How Does SIEM Empower Your Security Team?
🔹 Centralized Visibility: Correlates data from diverse tools (firewalls, endpoints, cloud) into a single pane.
🔹 AI-Powered Triage: Automates alert prioritization to reduce fatigue and accelerate investigations.
🔹 Playbook-Driven Response: Enforces consistent countermeasures against breaches.
🔹 Forensic Readiness: Preserves critical evidence for post-incident analysis.
Best-in-class SIEM solutions leverage machine learning, global threat intelligence, and customizable automation to transform raw data into strategic defense.
SIEM SERVICES
Tailored SIEM Solutions
for Every Business
✅ Fully Managed SIEM:
24/7 threat hunting, analysis, and response by experts.
✅ Co-Managed SIEM:
Collaborate with our specialists to augment your internal team.
✅ Cloud-Native Deployment:
Rapid implementation with AWS/Azure integration.
Global Reach,
Local Expertise
Regional SOC Hubs:
Strategically located across APAC (Hong Kong, Malaysia).
Elastic Cloud Analytics:
Scalable processing for evolving data volumes.
Threat Intelligence Fusion:
Real-time feeds from global cybersecurity alliances.
Future-Proof Security Outcomes
Grows with your business – no infrastructure constraints.
Risk Reduction:
Proactive threat hunting minimizes exposure and downtime.
Strategic Insights:
Executive-level reporting for informed security investments.
Accelerated Deployment:
Pre-built templates cut setup time
Why SIEM?
80%+ alert reduction via AI-driven filtering.
Compliance Simplified:
Pre-mapped frameworks (ISO 27001, GDPR, NIST).
Knowledge Transfer:
Upskills your team through joint analysis.
Proactive Roadmaps:
Anticipate threats with industry-specific intelligence.
MANAGED
SIEM SERVICES
Safeguard critical security data alongside business information.
Our solution ensures secure, immutable storage of SIEM logs with flexible retention policies.
Restore individual events or entire datasets seamlessly for forensic investigations or compliance audits.
2. Compliance & Security Automation
Turn SIEM into your compliance command center.
Achieve continuous compliance (ISO 27001, NIST, GDPR) with automated policy checks, real-time auditing, and pre-built reports.
Our multi-layered security integrates SIEM with threat intelligence for proactive defense.
3. Disaster Recovery & Cyber Resilience
Maintain visibility during disruption.
Real-time SIEM log replication and geo-redundant storage guarantee security monitoring continuity.
Rapid failover ensures incident response capabilities stay operational, minimizing breach impact.
4. Network Access & Threat Correlation
Detect lateral movement & credential threats.
We integrate SIEM with NAC solutions to correlate access events with security alerts.
Accelerate threat detection for compromised accounts, rogue devices, and policy violations across hybrid environments.
5. Intelligent Security Storage
Optimize cost & performance for security analytics.
Our tiered storage approach combines hot data for real-time SIEM analytics with
cost-effective cold storage for long-term retention and threat hunting – maximizing value without compromising speed.
6. Edge-to-Cloud SIEM
Extend visibility to distributed infrastructure.
Collect, process, and analyze security events at the edge with our lightweight agents.
Enable real-time threat detection for remote sites, IoT, and OT systems within your centralized SIEM.
What DELIVERS:
MANAGED SIEM EXCELLENCE
Proactive Threat Hunting:
Our experts use advanced SIEM analytics to uncover hidden threats before they escalate.
Intelligent Content Engineering:
Custom-built detection rules & playbooks tailored to your threat landscape.
Threat Intelligence Fusion:
Enrich SIEM alerts with real-time global threat feeds for context-rich detection.
Mature 24/7 Operations:
Fully managed SIEM monitoring, triage, and response by certified analysts.
Unified Security Fabric:
Seamlessly integrate SIEM with your existing cloud, network, and endpoint security tools.
Outcomes You Gain:
✅ Simplified compliance with centralized reporting & audit trails
✅ Lower operational costs via optimized log management & reduced alert fatigue
✅ Strategic security insights powered by actionable SIEM analytics
Innovative XaaS and
IT Management Solutions Architecture
Key Challenges Addressed by
Innovative XaaS and IT Management Solutions:
Rising Cyber
Threats
Protect exposed networks as businesses shift online, eliminating vulnerabilities with proactive threat detection.

Complex Tech Demands
Simplify operations with a unified platform that adapts to new technologies, reducing the burden on IT teams.
Workload Overload
Automate repetitive tasks like log analysis, configuration management, and performance tuning.
Skill Gaps
Leverage expert-driven solutions and a user-friendly portal to bridge talent shortages and standardize operations.
Smart essentials to make your ITSM wholesome
Make service management cross the boundary from IT to other business processes with the ITSM
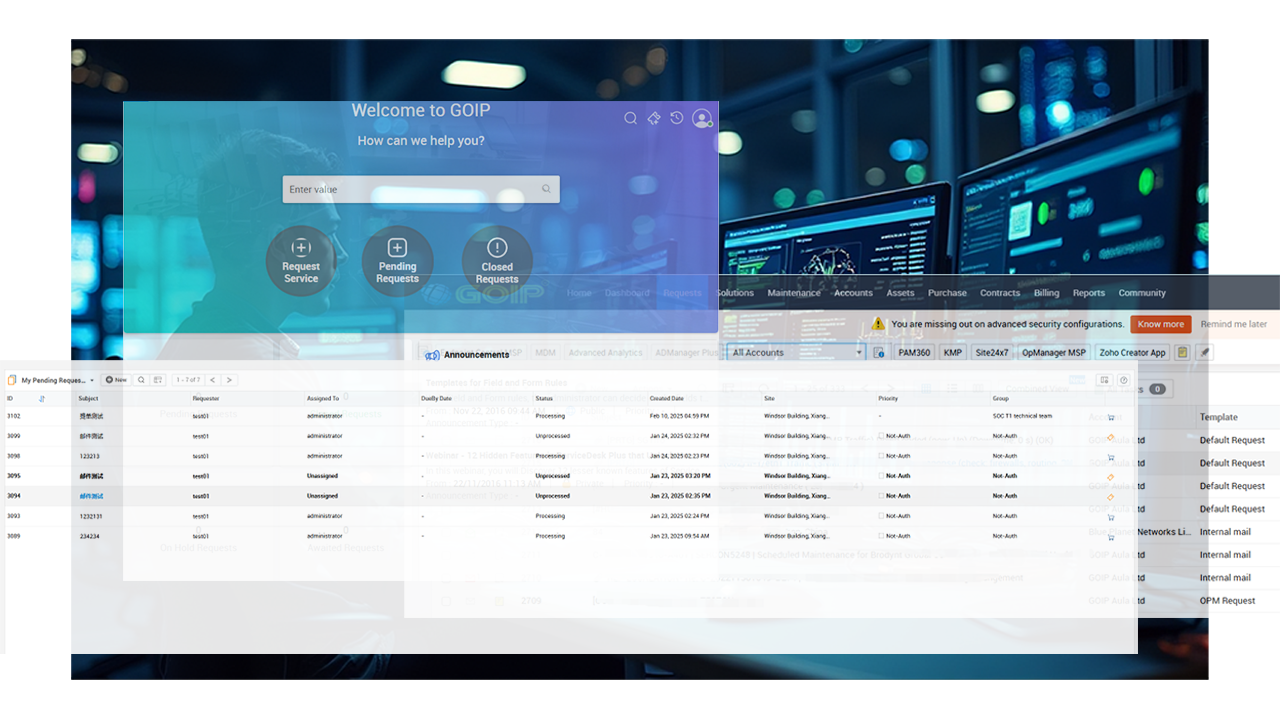
ITSM Platform
Overview:
ITSM is the “heart” of the Innovative XaaS and IT Management Solutions, serving as the core platform for managing customer network issues and incident reporting effectively. It provides a standardized operational method for Innovative XaaS and IT Management Solutions.
Key Features:
24/7 Instant Ticket Creation and Response:
Experience rapid ticket creation and processing that aligns with customer service agreements. Receive updates via email, SMS, and WeChat, while also allowing for web-based ticket tracking and history retrieval.
Network Management System (NMS)
Core Functionality:
The Network Management System is the central feature of the Innovative XaaS and IT Management Solutions, focusing on the operational stability and security monitoring of network devices. With 24/7 monitoring of customer-connected devices, it triggers response rules for instant ticket creation, connecting engineers to resolve issues and inform users.
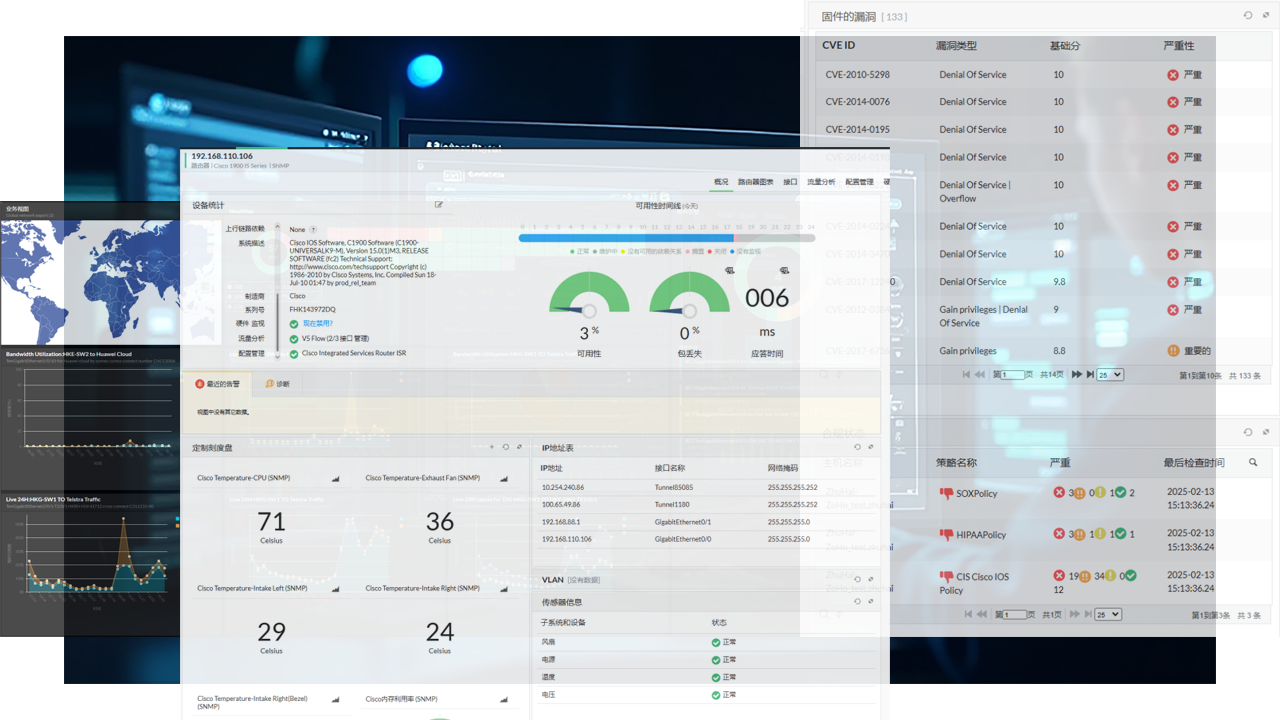
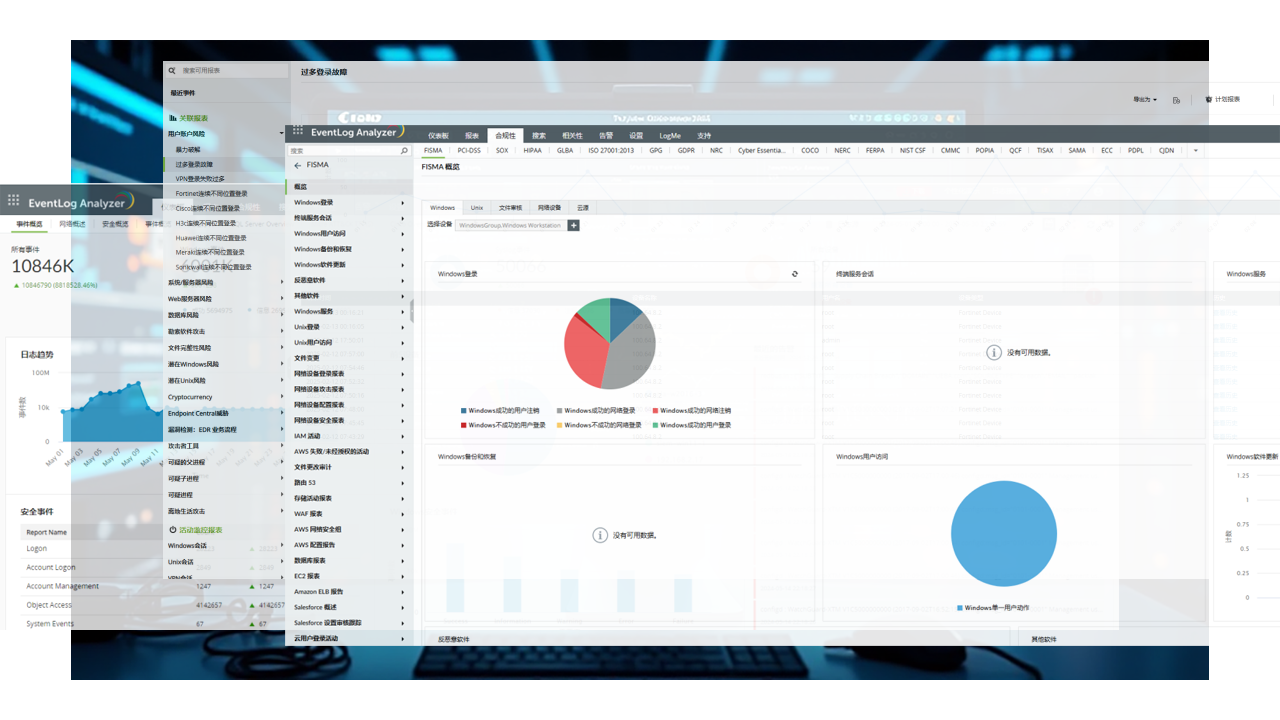
EventLog Analyzer Platform (ELA)
Security Analysis Tool:
EventLog Analyzer Platform is a critical component of the S.NOC solution for network security analysis. It collects logs from servers, network devices, security equipment, and application systems to conduct thorough security assessments.
The platform offers compliance checks for network security and performs standard baseline security evaluations on devices. It integrates with the ITSM system to set response rules for instant ticket creation, facilitating timely issue resolution and user notifications.
Why Choose Innovative XaaS and IT Management Solutions?
Unlocking Your Business Potential
Continuous oversight of devices, traffic, and logs for instant anomaly detection.
Automate workflows, generate real-time reports, and resolve incidents faster.
Track every action with a dedicated dashboard for audits, compliance, and transparency.
Security
Stay ahead of threats with AI-driven analytics and adaptive response protocols.





