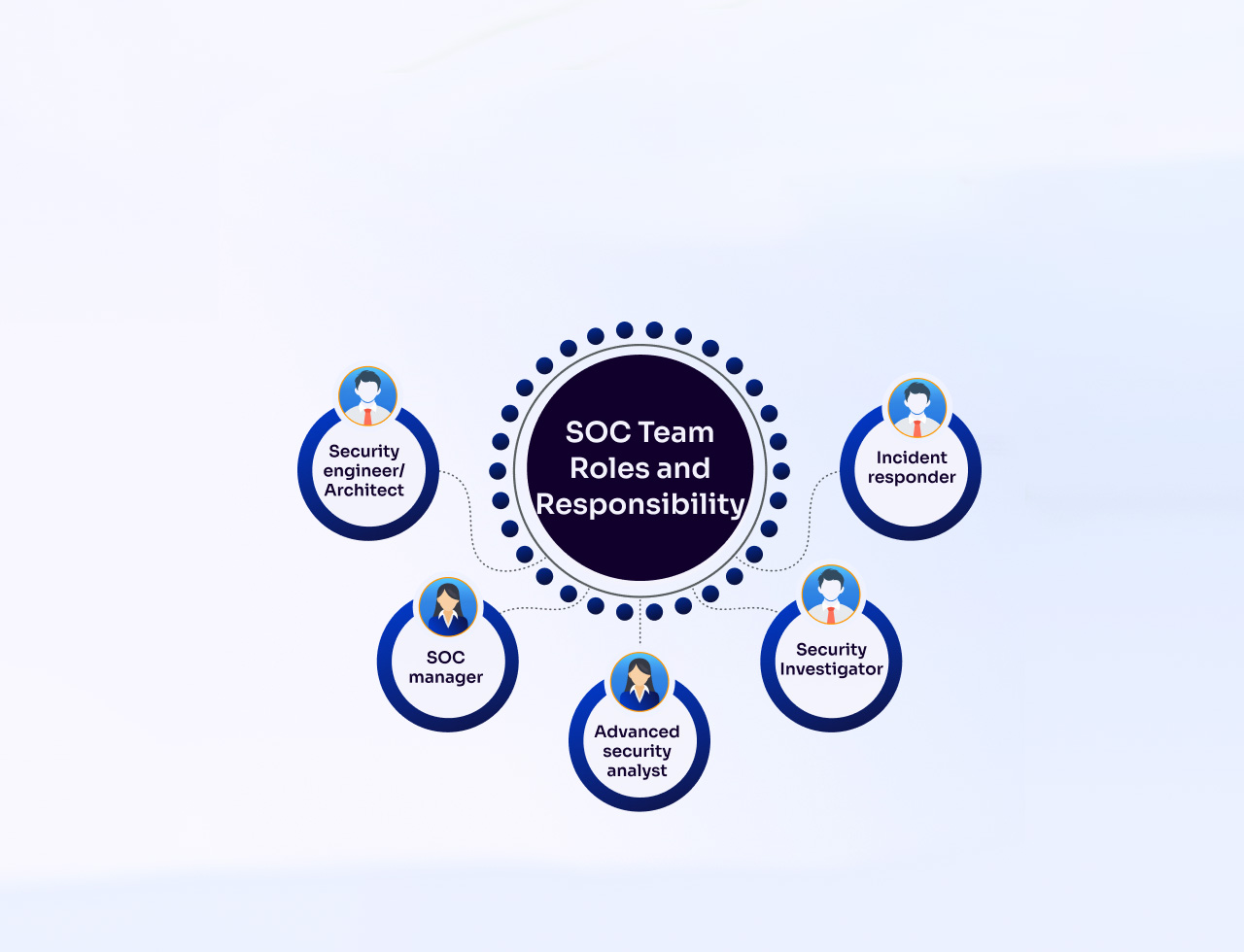
Understanding SOC Team Roles: Tiers, Responsibilities & Specializations
A Security Operations Center (SOC) is the nerve center of an organization’s cybersecurity strategy, integrating people, processes, and technology to detect, analyze, and respond to threats. At NCDefence, we break down the critical roles within a SOC—from frontline analysts to specialized hunters—and how they collaborate to fortify your security posture.
Core SOC Team Structure
1. Tier 1 — Triage Specialist
- Responsibilities: Monitor alerts, validate threats (filtering false positives), prioritize incidents, and escalate unresolved issues.
- Key Skills: Alert management, basic threat analysis, and security tool configuration.
- Goal: Rapid initial response to minimize alert fatigue and ensure critical threats move up the chain.
2. Tier 2 — Incident Responder
- Responsibilities: Investigate escalated threats using threat intelligence, contain attacks, and initiate recovery.
- Key Skills: Incident analysis, threat correlation, and mitigation strategy development.
- Goal: Resolve complex incidents and transform raw data into actionable intelligence.
3. Tier 3 — Threat Hunter
- Responsibilities: Lead advanced threat investigations, conduct vulnerability assessments, and uncover hidden risks.
- Key Skills: Proactive threat hunting, penetration testing, and security optimization.
- Goal: Identify and neutralize sophisticated threats before they escalate.
4. SOC Manager
- Responsibilities: Lead advanced threat investigations, conduct vulnerability assessments, and uncover hidden risks.
- Key Skills: Proactive threat hunting, penetration testing, and security optimization.
- Goal: Identify and neutralize sophisticated threats before they escalate.
Specialized SOC Roles
- Malware Analyst: Reverse-engineers malware to aid investigations and improve defenses.
- Threat Hunter (Specialized): Proactively scans networks for undetected threats using threat intelligence.
- Forensics Specialist: Investigates cybercrimes and analyzes digital evidence.
- Vulnerability Manager: Identifies and remediates system weaknesses.
- Security Architect/Consultant: Designs robust security infrastructures and benchmarks SOC capabilities against industry standards.